Polymorphic XOR in-memory Decoder (Win64)
Description
The polymorphic feature provides a multi layer protection from evasion:
- The raw payload will be encoded by
XORwith your custom key - The encoded payload will be appended to the
XOR-decoder-stub1 - Your custom key will be replaced in the stub and appended to EOF
- The final shellcode will be written to disc
After injection, the stub will decode your payload bitwise, until a NULL-byte is found.
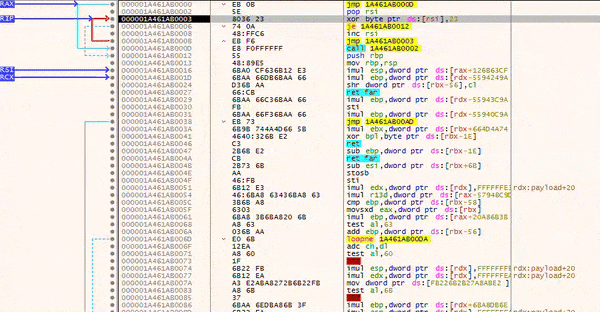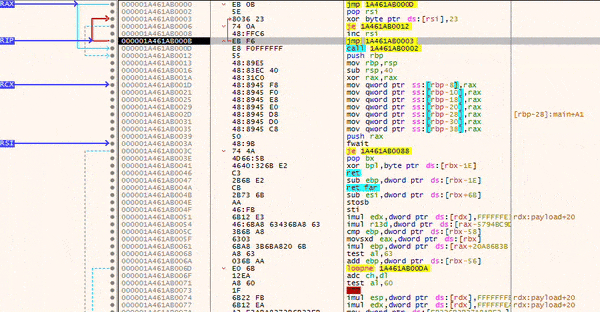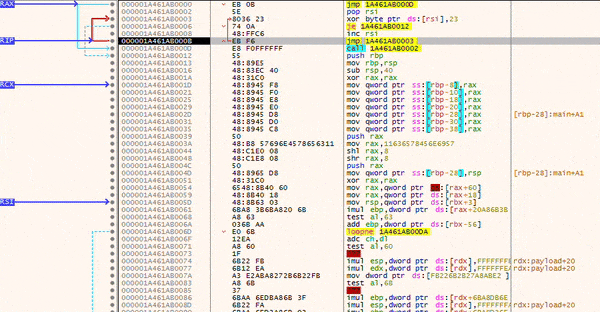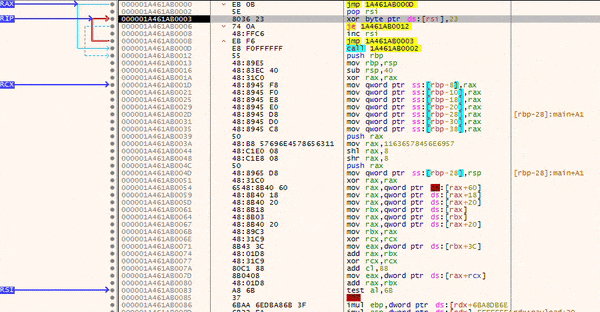
Once the decoding is done, your payload will be executed.
Command
python shencode.py xorpoly --input xor-encoded.raw --output output.raw ---key 63
shencode encoder xorpoly [-h] [-i INPUT] [-o OUTPUT] [-k KEY]
options:
--help show this help message and exit
--input INPUT Input file for XOR stub
--output OUTPUT Outputfile for XOR stub
--key KEY Key for XOR stub
Example output
shencode encoder xorpoly --input calc.xored --output calc.polyxor ---key 63
[+] [XOR-POLY] File exists
[i] [XOR-POLY] File: calc.xored
[i] [XOR-POLY] Hash: d647a0071c9402d21a4c68392d3c77b7c921e33d
[85, 72, ... 195]
[*] Header loaded, size of shellcode 18 bytes
[*] XORed payload added, size of shellcode 269 bytes
[+] XOR encoded shellcode created in calc.polyxor
[+] [XOR-POLY] File created
[i] [XOR-POLY] File: calc.polyxor
[i] [XOR-POLY] Hash: cb0504a65ce35ea76e941c39708749858930df28
Resources
-
the stub is based on Ray Doyles work check this article ↩